Table of Contents:
![]() The Rise of Remote Work Has Dramatically Raised the Cybersecurity Table Stakes
The Rise of Remote Work Has Dramatically Raised the Cybersecurity Table Stakes
![]() Where Are Cyber Threats Coming From?
Where Are Cyber Threats Coming From?
![]() What is Managed Detection and Response, and Why Do You Need It?
What is Managed Detection and Response, and Why Do You Need It?
![]() What Happens When MDR Detects a Cyber Threat?
What Happens When MDR Detects a Cyber Threat?
![]() How to Incorporate MDR into Your Current Security Stack Through Securus360
How to Incorporate MDR into Your Current Security Stack Through Securus360
![]() Other Ways You Should Be Protecting Your Business
Other Ways You Should Be Protecting Your Business
![]() The Preventative Cyber Protection AND Real-Time Detection Your Organization Needs
The Preventative Cyber Protection AND Real-Time Detection Your Organization Needs
The Stakes are High
On September 30th, 2021, October was officially declared Cybersecurity Awareness Month to “elevate the central role that cybersecurity plays in our national security and economy”. 2021 has seen some of the most significant adversarial cybersecurity events ever recorded. From the Kaseya, Colonial Pipeline, Twitch, and SolarWinds incidents, there are many lessons IT leadership needs to incorporate into their security strategy going forward.
Senior IT decision-makers, chief information security officers (CISO), and other C-suite executives concerned with successfully mitigating an ever-growing assortment of risks face an incredibly challenging environment. Many do not believe in their organization’s ability to counter modern attacks successfully. The 2021 Voice of the CISO Report found that 64% of CISOs fear their organizations will be targeted by reputation-destroying cybercrime in the coming years—and 66% feel they are in no way prepared to limit and contain damages from such an attack.
Cyber attacks have increased 600% since the beginning of the COVID-19 pandemic, and criminal organizations are more brazen than ever before. National Security Agency Director Paul Nakasone recently spoke out to sound the alarm that ransomware attacks are not slowing down, in fact they are increasing and targeting American businesses of all sizes and across every industry.
Fighting Back Against Cybercrime
Currently, most organizations are using a wide variety of different tools to secure their networks without genuinely harnessing the ability to effectively identify their cybersecurity blindspots. To develop the defensive capabilities needed to thwart modern attacks, it is essential to implement an all-inclusive network security monitoring solution to deliver threat visibility across your entire digital infrastructure: endpoints, servers, network, cloud instances as well as end-user behavior, all through a single pane of glass and platform.
The global cybersecurity industry is worth $217 billion in 2021, though experts believe this will grow to $345.4 billion over the next five years. The need for comprehensive solutions to protect global workforces and safeguard sensitive information has never been greater. Today, cyber resilience requires moving beyond prevention and developing sophisticated detection capabilities to successfully contain advanced persistent threats (APT) before they explode out of control.
The clock is ticking, and time is running out. Cybercriminals are motivated to take advantage of the global shift towards remote work, and organizations in every industry increasingly find themselves within the crosshairs of attackers.
By the end of 2021, the associated costs, damages, and lost revenues caused by global cybercrime is expected to reach $6 trillion, though as soon as 2025 could exceed $10.5 trillion. Intrusions are increasing all the time, and it is no longer a matter of if, simply a matter of when. Your organization will eventually face these threats, with the potential for all your hard work to be erased in the blink of an eye.

The Rise of Remote Work Has Dramatically Raised the Cybersecurity Table Stakes
In the wake of the global pandemic, organizations implemented far-reaching digital transformation initiatives to successfully transition 70% of the full-time workforce to work at home. As we move towards a post COVID world, 58.6% of workers are expected to continue working remotely.
At the center of the rise in remote work is the adoption of software as a service (SaaS) solutions, cloud-powered storage systems, and bring your own device (BYOD) policies that have exponentially exposed organizations to cyber risks. According to Gartner, end-user spending on public cloud based storage reached $396 billion in 2021, though it is expected to rise to $480 billion by next year.
It’s absolutely no coincidence that a global crime wave has been unleashed in direct correlation to vast quantities of workers and valuable data sets migrating to access points that attackers can more easily penetrate. The new landscape of social engineering and phishing scams makes it extremely simple for just a single misplaced mouse click to lead to tragic and costly consequences.
Though many workers flourish in remote working environments, others struggle to maintain productivity when working from home. Distractions can easily lead to mistakes and breaches of protocol. Companies that have established strong information security best practices are seeing them erode daily, while IT leadership has limited insight into what remote workers are doing.
There is nothing wrong with shifting to cloud-based services, and in fact, it seems likely that digital transformation completed during the pandemic will stay with us long after it has finished. The key is developing more comprehensive information security practices to mitigate the new risks posed by remote work, and the use of SaaS solutions and cloud-powered storage solutions.
Criminals find it easier and easier to complete lateral movements originating from actions completed across unsecured devices and networks. In the next section, learn a bit more about where modern cybersecurity threats are emerging from.
Where Are Cyber Threats Coming From?
Most businesses do a great job of prevention, but like putting all new locks on your house doors and windows, a thief that finds the key under the mat is still going to get in your house. The main problem with relying on a prevention-only-based approach to cybersecurity is the likelihood that you will be hit with a polymorphic or metamorphic strain of malware.
Information security researchers suggest that 97% of all malware deployed globally is polymorphic. Due to this quality, prevention-based systems are unlikely to notice anomalous behaviors before they lead to tragic outcomes for your organization. Businesses need to find intrusions and take swift action to isolate them and limit the ability for a single breach to escalate out of control. Some threat examples include:
- Data Exfiltration: The process of initiating an unauthorized data transfer between a network device and an attacker's network device.
- Lateral Movement: Attackers gain access to a digital network and seek to initiate additional processes that will provide them access to other network settings, platforms, and targets.
- Low and Slow Attacks: This type of attack mimics normal data usage in effort to avoid triggering alarms.
- Internal Reconnaissance: When an employee is purposefully seeking access to files, datasets, or information that they are not supposed to have access to.
- Social Engineering: These tactics continue to become more and more advanced using emails, messaging applications, and social media sites to deliver deceptive messaging.
- Unique Signatures: The presence of a unique signature is one of the features used to describe a polymorphic or metamorphic malware strain.
- User Branch: This occurs whenever an authenticated user creates unnecessary risks by either not following cybersecurity best practices or intentionally compromising security for malicious purpose.

Who is Cyber-Attacking?
Modern cybercriminals come in all shapes and sizes. You will find everything from opportunistic individuals seeking to earn easy money to the worst of the worst organizations dedicated to profit from every type of illicit activity imaginable. In many cases, the individuals and groups behind APTs are likely to be state-backed agents working on behalf of foreign governments.
There is evidence of cyberattacks launched as a part of corporate espionage and compromise campaigns designed to weaken competitors' positions using illegal cyber intrusion methods. Regardless of where attacks originate or who is launching them, your organization has a vested interest in mitigating threats to protect your reputation and future profitability.
What is Managed Detection and Response, and Why Do You Need It?
Managed detection and response (MDR) is a means of outsourcing cybersecurity expertise to reduce costs while delivering much more rigorous and advanced cybersecurity practices by harnessing advisory services that vastly extend the reach of your in-house IT team.
A qualified managed detection and response service provider is able to deliver prevention-based processes meant to limit the potential for cyber threat actors to gain access to your digital networks. By actively threat hunting, your MDR service provider operates 24-7 to ensure any exploitation attempts are stopped in their tracks before they can grow into a reputation-destroying event.
The active component of MDR and its ability to constantly scan activity across your network for signs of unusual activity and compromise is what sets it apart from more traditional solutions. Many organizations believe they have this aspect covered because they have secured high-quality prevention-based cybersecurity services.
Prevention and Detection
It is essential to implement both prevention and detection-based cybersecurity strategies to mitigate known threats and those with unique signatures and polymorphic design features. In today's threat environment, prevention-based protection is useful, but it is simply not enough to reduce the risk posed by data breaches, ransomware, phishing scams, and other sophisticated cybercrime.
In-house security efforts are complemented tremendously by advanced detection-based processes that work to analyze your digital networks proactively. These processes isolate abnormal activity and aggressive lateral movements across your networks and constrain them before they grow into more serious and detrimental cyber-attacks.

What Happens When MDR Detects a Cyber Threat?
Network Managed detection and response (MDR) services prepare your organization to identify, contain, and remediate attacks through an integrated system that provides all relevant information regarding an attack on a single pane of glass and becomes the source of truth for interpreting cybersecurity alerts and incidence reports.
MDR allows you to constantly hunt for new threats using active detection protocols. Threat hunting uses machine learning to quickly identify anomalous and unexpected behaviors to gain insight into normal network usage. Your outsourced cybersecurity support team then analyzes incoming alerts to ensure your staff has all the necessary information to stay ahead of evolving issues.
Notification
With an MDR solution, you can say goodbye to alert fatigue. Instead of constantly having everyday non-threat activities trigger security notifications that do not provide any contextual insight or true protection, an MDR platform helps weed through the noise, with alerts validated by human cyber analysts before being sent to your IT organization, so your team only spends their limited time on valid alerts that require investigation.
Halting Attacks & Auto Containment
A robust MDR solution goes far beyond merely hunting for cyber threats and also contains advanced capabilities for stopping attacks, limiting the ability for lateral actions to result in further compromises. This is usually achieved through an auto containment process utilizing advanced automation to implement security protocols as issues are identified.
Remediation
Proper automated incident response and remediation processes should also be a part of a good MDR solution that secures your organization against cybersecurity threats. Managed detection and response services should integrate with your existing security stack, overlap, and even offer the potential to consolidate security services.
How to Incorporate MDR into Your Current Security Stack Through Securus360
Integration
Securus360's MDR offering is a fully integrated solution that works powerfully alongside your existing security stack while providing the increased visibility and mitigation capabilities necessary to limit a cyber risk threatening your organization.
Securus360 adds immense value to security processes by offering a much more comprehensive and cost-effective solution than other providers. This is accomplished by adding a comprehensive, multilayered protection and detection set of processes that give 360° visibility and awareness of your organization’s threat environment, in real-time.
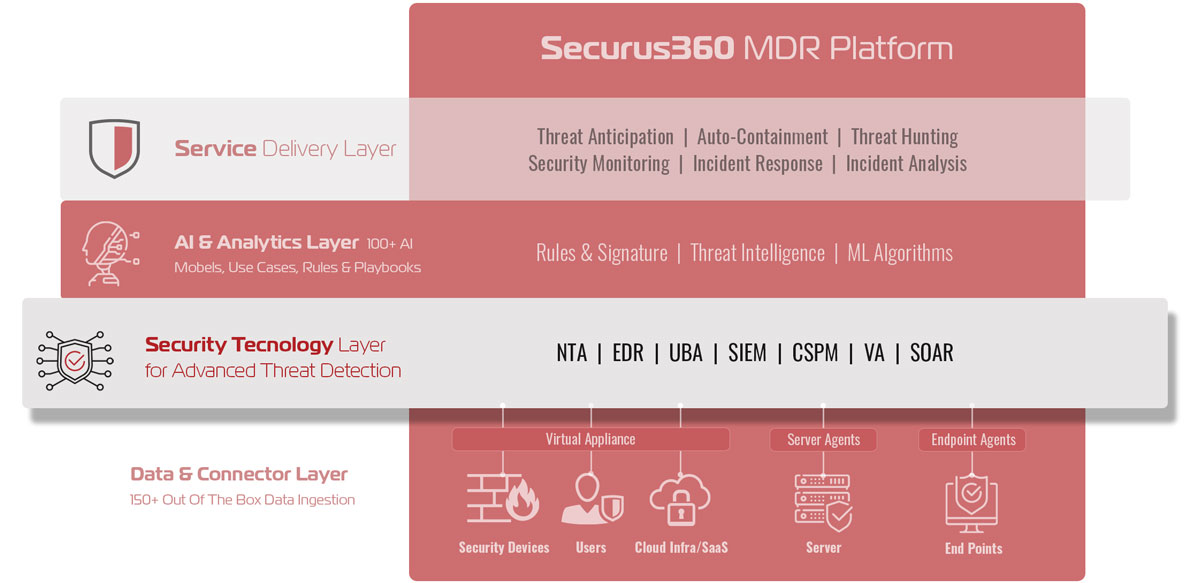
Overlap & Consolidation
Securus360's design is to work alongside and overlap with all modern cybersecurity platforms and services. We deliver everything your organization needs with a truly scalable all-in-one security solution, allowing customers to consolidate their security services within a single platform, providing that single pane of glass and source of truth view that eliminates the blind spots currently plaguing businesses of all sizes.
Securus360 leverages a 21-point security event notification checklist that thoroughly vets any notification sent to your security dashboard. Our industry-leading MDR dashboard vastly enhances the surface area that can be seen, protected and safeguarded.
We proudly offer a fully integrated and comprehensive prevention and detection-based MDR solution that enables your organization to counter the threats of today and anticipate the challenges of tomorrow.

Other Ways You Should Be Protecting Your Business
Borderless Networks
Increasingly, organizations are operating with remote work as the new normal. That means your workers, partners, and customers are more likely to interact with your company across nearly unlimited entry points across what are essentially borderless networks.
While in the past, it was feasible and straightforward to create network-wide security protocols covering activities taking place across a dedicated campus, today's work is taking place at many different unsecured locations, increasingly across employees’ personal electronic devices.
Continuous Employee Training
Your organization must develop provisions for managing your new landscape of borderless networks to mitigate modern cybersecurity threats. Accomplishing this requires developing continuous training programs for staff and setting up policies to ensure best practices are being followed by every worker at all times.
BYOD Policies
One of the most important policies for remote organizations to develop is managing the Bring Your Own Device (BYOD) segment of employees. In many cases, remote workers are now conducting regular business across their personal devices. This increases the need for policies and training to ensure that these devices do not become vulnerable attack vectors for cybercriminals.
The Preventative Cyber Protection AND Real-Time Detection Your Organization Needs
It’s clear that today there has never been a more persistent and advanced cyber threat environment aimed directly at American businesses.
Incidents such as SMS phishing scams have increased by as much as 700% this year. Phishing attempts account for as much as 91% of all cyber-attacks leading to data breaches and 83% of all attacks registered against organizations worldwide. Internationally, the average cost of a single data breach is estimated to be $3.84 million, though, in the United States, the average cost is closer to $8.64 million.
Ransomware attacks have received huge amounts of international press in recent years due to high-profile attacks that have brought many Fortune 500 companies to their knees. Experts believe ransomware increased by 1,318% since 2020 when the global pandemic began. This year the cost of ransomware is expected to top $20 billion, though by 2035 is projected to reach $265 billion.
New cyber attacks are occurring every 11 seconds in 2021. Once attackers gain access to your network, they will seek to complete lateral movements to gain further traction and access your most sensitive data. If your organization relies on a protection strategy that hinges on prevention-based cybersecurity, you are not prepared to counter the east-west movements that modern attackers are using.
IT Leaders Need to Act - Even the Big Guys Are Getting Hit
You can sit back and hope that a single employee misstep or misconfigured network setting doesn't lead to tragedy. But the harsh truth is that no matter what industry you are in or what security protocols you have in place, they can all fail, and the results can be absolutely devastating.
In 2016, one of the most severe cyber attacks of all time was unleashed against Dyn, a company formerly responsible for much of the internet's domain name system registry (DNS). The company was quickly brought to its knees when levied with a series of distributed denial of service (DDoS) attacks. As a result, websites and platforms for companies including Twitter, Amazon, Netflix, GitHub, PayPal, Pinterest, the Guardian, and Fox News went down immediately.
Every day, more and more private and public organizations face cyberattacks. It is only a matter of time before your organization falls victim. Cybersecurity is a strategic investment that helps ensure your organizations ability to enjoy success and maintain profitability long into the future.
The Tools and Expertise You need
Instead of relying on a patchwork coalition of external security applications—implement a solution that places your entire security operations command into a single platform— creating a unified source of truth. Hire our industry-leading cybersecurity experts and prepare your organization to counter the threats of today to realize the opportunities of tomorrow.




