Increased Dependence on Technology
Increased Dependence on Technology Leads to InfoSec Blind Spots - Today’s organizations of all...
Platform for Cyber Analytic & Hybrid SecOps
Data Protection ▼Secure Your Data From Potential Threats
High Speed Cyber Defense to Thwart Threats in Real Time
Service Comparison ▼See How MXDR Compares to Other Platforms
Our experts weigh in on the cybersecurity landscape
What Superintendents Need to Know ▼Protect Your School District, Your Students, and Your Staff With Highly Specialized K-12 Cybersecurity
Our insights into complex cybersecurity challenges
Ransomware Calculator ▼How Much Could a Ransomware Attack Cost Your Business?
14 years of experience in Data Protection, Cybersecurity & Compliance.
Blind Spot ▼Short video on the problem we solve
It’s a Shared Responsibility - Be sure you are Protected - Concerns over cloud security have dominated the adoption of cloud computing over the past few years. Despite the extensive adoption of digital transformation, many enterprises are yet to fully integrate cloud computing for mission-critical applications due to apprehension and concern over the security of information stored and transferred over the cloud.
For their part, cloud service providers, such as Amazon, argue that cloud solutions are just as secure, if not more secure, than on-premise, organization-based configurations. In a recent shareholder letter, Jeff Bezos, Amazon founder and CEO, elaborated on the many ways the industry’s most extensive public cloud is secure. “The ability for organizations to access the scalable, dependable, and highly secure computing power – whether for vital healthcare work, to help students continue learning, or to keep unprecedented numbers of employees online and productive from home – is critical in the current situation,” Bezos said about the vital role Amazon is playing in the COVID-19 crisis. “Governments are leveraging AWS as a secure platform to build new capabilities in their efforts to end this pandemic.”
Regardless of what one believes, it is vital to get the facts right. It is certain Amazon does not offer out-and-out security measures for Amazon Web Services (AWS). To understand how organizations can ensure they are protected, let's quickly review what the AWS platform is all about.
AWS is a cloud-based security platform that offers database storage, compute power, content delivery and other functionality. The platform has proven value and has become essential in helping many businesses scale and grow with little to no friction.
Put simply, AWS helps organizations do the following:
AWS offers users a wide range of global cloud-based products such as developer tools, enterprise applications, storage, analytics, and networking. Currently, AWS has over 175 fully featured services for a wide range of technologies, industries, and use cases. Amazon revealed that the number of active AWS users exceeds 1,000,000. Organizations that integrate AWS within their operational and management processes benefit by lowering IT costs, scaling and moving faster. Indeed, large enterprises and start-ups trust AWS to power a wide range of workloads.
The problem with AWS is that the cloud service provider does not provide full security measures for the platform. This conclusion can be derived from the numerous high-profile AWS breaches reported this past year by large companies including eBay, Shopify, PayPal and Stripe where a total of eight million records were involved. Other high profile breaches include Accenture, Uber and Time Warner Cable.
Let us look into some of the breaches to understand better why enterprises need to ensure they are protected rather than relying on AWS without full security measures.
High-profile AWS Breaches
Accenture, a cloud technology leader, fell victim to AWS breaches when the organization inadvertently left its AWS S3 buckets open to the public. This costly error allowed any user to download organizational content. The unsecured buckets contained confidential customer information, client certificates and API data. Meanwhile, the backup database, which was also left vulnerable, contained almost 40,000 passwords, mostly in plain text. The mistake also exposed Accenture’s secret decryption keys and software for the cloud platform. Hackers could have accessed this information and used it to compromise the organization or its clients.
One of the biggest AWS security breaches happened a few years ago when a misconfiguration resulted in the disclosure of personal information of about 4 million Time Warner Cable customers. Nonetheless, the information was not accessed by actors with malicious intent. Security researchers investigating a breach related to World Wrestling Entertainment discovered the incident and concluded that it resulted from configurations that permitted public access. Two Amazon S3 buckets possessed SQL databases that contained customer billing addresses and contact information. No evidence suggested that any credit card information had been exposed. This security incident could have been avoided by reviewing the permissions applied to the S3 buckets.
Another company affected by susceptible AWS security measures has been Uber. This incident received extra attention due to a combination of the attack’s nature and the organization’s response. Uber became infamous for bribing the hackers with $100,000 to keep the incident that affected more than 57 million customers a secret. Hackers gained access to the company’s private GitHub account and proceeded to extract the AWS credentials.
In yet another incident, according to breach hunter Bob Diachenko, an exposed AWS server containing the MongoDB database became visible on February 3, 2020, and it remained indexable for five days. Security researchers also discovered 22 AWS application programming interfaces (APIs) across 16 AWS services that hackers can leverage to leak information. Cybercriminals can abuse the AWS APIs to leak AWS Identity and Access Management (IAM) users and roles in arbitrary accounts across AWS, AWS-US-Gov, or AWS-Cn. Attackers can abuse a wide range of AW services, including Amazon Simple Storage Service (S3), Amazon key Management Service (KMS), and Amazon Simple Queue Service (SQS).
These and other cases demonstrate the vulnerability of Amazon’s AWS platform due to improper configuration of security tools or the absence of full security measures.
The Shared Responsibility model means that Amazon DOES NOT accept total responsibility to protect your AWS deployments. According to this model, compliance and security is a shared responsibility between the customer and AWS. In this case, the cloud service provider is responsible for operating, managing and controlling components. However, this responsibility is only exercised from the virtualization layer and host operating system to the facilities’ physical security. The customer assumes managing the guest operating system, updates, security patches, application software, and the security firewall configuration. It is important to note that customer responsibilities depend on the services used. Consequently, they must carefully consider the services they opt for.
The figure below summarizes the primary responsibilities shared between AWS and the customer:
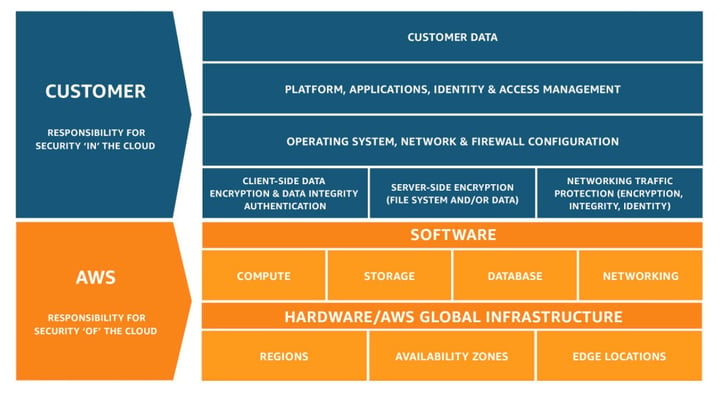
Figure 1: Shared responsibilities between AWS and the customer
Amazon does not offer full security measures for your cloud workloads in AWS. Azure has similar issues, and as such, companies must take responsibility for their cloud security. The three key questions that they must consider before outsourcing are:
Companies must understand that cloud security is a shared responsibility, especially if they rely on third-party service providers to deliver or support core services and protect sensitive data. In this way, the organizations will comprehend that Amazon does not offer complete security measures for their AWS deployments. That is to say, cloud providers are only responsible for the security “of” the cloud, in which case companies must be responsible for security “in” the cloud. The companies should not confuse their cloud provider’s compliance with their own. In an analogy, consider staying at a hotel; the security guard is responsible for protecting access to the hotel and the lobby. Meanwhile, the customer is responsible for securing their rooms and valuables.
The following strategies can help companies assume responsibility and ensure their protection in AWS:
It remains difficult for users of AWS and other cloud platforms to securely benefit from cloud offerings while navigating the security blind spots inherent with those solutions. Fortunately, businesses can partner with cybersecurity leaders like Securus360 to protect their AWS instances. We tailor each specific Managed Cloud Security Service to the unique requirements of each organization to comprehensively monitor all Cloud connections and assets 24x7. Our solution secures the cloud configuration and remediates risks across the entire cloud infrastructure. Securus360 provides an all-inclusive network security monitoring solution that offers the industry’s most effective, fully integrated platform that delivers threat visibility across all cloud instances. With Securus360 organizations can leverage the agility of the cloud with the peace of mind that their deployments are fully monitored and secure.
Contact Us to Learn More!
Increased Dependence on Technology Leads to InfoSec Blind Spots - Today’s organizations of all...
How to Ensure You Have Complete Visibility to Cyber Threats - The primary foundation of a cloud...
Copyright © 2025 Securus360 | Privacy Policy | Cookie Policy | Terms and Conditions | Disclaimer